Neben Brute Force Attacken tauchen immer wieder SQL Injections auf der Liste der größten Gefahren für WordPress Websites auf. Es handelt sich dabei um relativ einfach durchzuführende Manipulationen an der Datenbank deiner Website. So kommt man an sensible Daten oder richtet sich selbst Admin Accounts ein und kann eine Website nach Belieben manipulieren. Wir zeigen, wie der Angriff funktioniert und warum er so gefährlich ist.
Im März 2008 wurden 134 Millionen Kreditkartendaten beim amerikanischen Konzern Heartland Payment Systems ergattert, unter anderem von einem wahren Mastermind. Dieser Angriff beruht auf einem relativ einfach auszuführenden Hack namens SQL Injection. Bei diesem Angriff wird Zugriff auf die Datenbank einer Website erhalten und somit auf alle Daten einer Website. Tatsächlich gelten SQL Injections deshalb als eine der größten Gefahren für Websites – auch und vor allem für Personen, die hauptsächlich mit WordPress arbeiten.
Und da spätestens seit WooCommerce insbesondere auch größere und komplexere Shops problemlos mit WordPress betrieben werden können, ist es wichtig zu verstehen, wie hoch das Risiko einer WordPress SQL Injection ist und wie diese funktionieren.
WordPress SQL Injections – wie gefährlich sind sie?
Die Frage nach der “Gefährlichkeit” eines WordPress Hacks kann nicht in Form eines einzigen Indikators beantwortet werden. Vielmehr muss man mindestens zwei Aspekte betrachten: Zum einen die Wahrscheinlichkeit, mit der das eigene WordPress Projekt einem solchen Angriff zum Opfer fallen kann, sowie den Schaden, den ein Hack verursachen kann.
Bei Brute Force Attacken ist etwa die Zahl der monatlich gefahrenen Attacken so hoch (teils über 1 Milliarde gemessene Angriffe + Dunkelziffer), dass man eigentlich sagen kann: Jede WordPress Website gerät früher oder später ins Visier einer solchen Attacke. Der Schaden, der durch einen erfolgreichen Hack entstehen kann, ist mannigfaltig. Meist dienen Brute Force Attacken auch dazu, Websites zu kapern und in ein Botnet einzubinden. Cross Site Scripting hingegen kommt wesentlich seltener vor, dient aber vor allem dazu, Websites mit Schadcode zu infizieren.
Die Non Profit Organisation Open Web Application Security Project (OWASP) gibt regelmäßig eine Top 10 Liste der größten Sicherheitsrisiken für Webanwendungen heraus. Und SQL Injections belegten hier in der Vergangenheit dauerhaft den ersten Platz, seit 2021 sind sie “nur” noch auf Platz 3.
Tatsächlich sind SQL Injections gekommen, um zu bleiben. Der Hack ist seit mittlerweile über 20 Jahren bekannt. Auch die Häufigkeit von SQL Injections stieg im Laufe der Zeit.
Wordfence, Hersteller einer Sicherheitssoftware für WordPress, kommt zu dem Ergebnis, dass SQL Injections speziell für WordPress Websites eine große Gefahr darstellen. Eine Analyse von knapp 1.600 Sicherheitslücken in Plugins, die über einen Zeitraum von 14 Monaten gemeldet wurden, zeigt deutlich, dass SQL Injections das zweithäufigste Sicherheitsrisiko überhaupt für WordPress Websites sind.
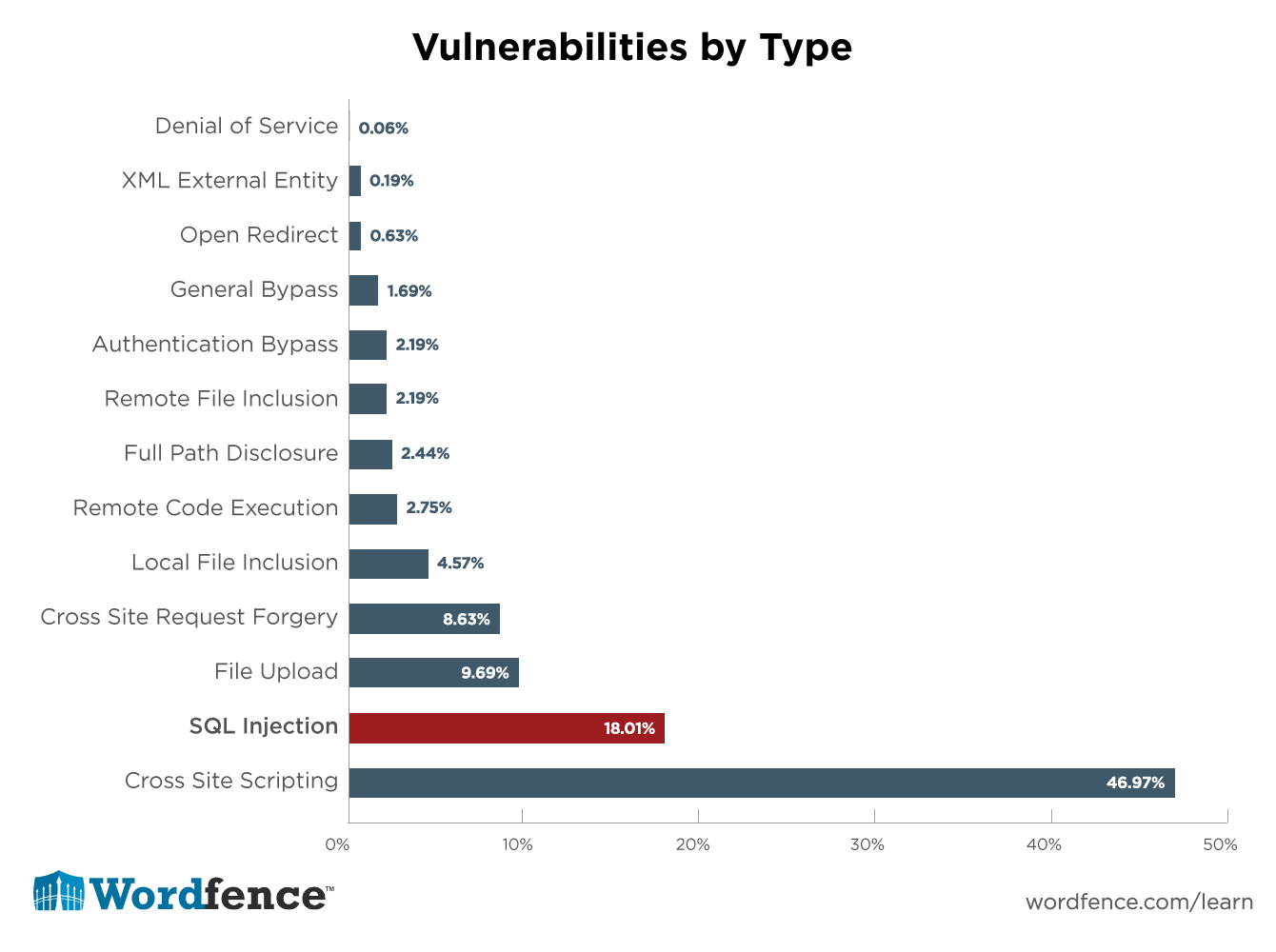
Bei all diesen Zahlen musst du dir natürlich vor Augen führen, dass die Dunkelziffer wesentlich höher ausfällt – häufig werden SQL Attacken gar nicht bemerkt und tauchen dann in keiner Statistik auf.
Die Zahlen zeigen, dass WordPress SQL Injections nach Brute Force Attacken und XSS Lücken zu den häufigsten Angriffsarten überhaupt zählen. Zudem nehmen SQL Injections einen besonders sensiblen Bereich deiner Website ins Visier: deine Datenbank. Insbesondere für Shops sind diese Hacks somit eine existenzielle Bedrohung. Daher ist es wichtig zu verstehen, wie sie funktionieren und was du dagegen tun kannst.
WordPress SQL Injections zielen auf das Herz deiner Website
Um zu verstehen, wie eine SQL Injection funktioniert, muss dir klar sein, wie WordPress grundlegend aufgebaut ist. Wenn du das bereits weißt, kannst du diesen Abschnitt getrost überspringen.
Die Datenbank ist die Basis für jede WordPress Installation: Alle Inhalte sind hier abgelegt. Das CMS selbst ermöglicht es dann, diese Inhalte darzustellen und zu bearbeiten. Bei WordPress handelt es sich um eine MySQL Datenbank. SQL steht für Structured Query Language, eine Programmiersprache mit vollem Funktionsumfang, mit deren Hilfe Strukturen in einer Datenbank angelegt und Daten eingefügt, verändert und gelöscht werden können.
Jedes Mal, wenn du einen Artikel schreibst, eine neue Kategorie anlegst, dein Passwort änderst oder auch wenn ein Kommentar geschrieben wird, werden diese neuen Daten in der Datenbank abgespeichert. Hier liegt also jeder einzelne Inhalt deiner Website.
WordPress zieht sich immer, wenn deine Website aufgerufen und bestimmte Inhalte angefordert werden, die passenden Daten aus der Datenbank, bringt sie mit PHP zusammen und erstellt ein HTML Dokument, das schlussendlich an den Browser des Clients übertragen wird. Von den ganzen Vorgängen, die bis dahin stattfinden, bekommt der Client nichts mit.
SQL Injections schleusen externen Code in die Datenbank
Auch wenn du selber nie direkt mit der Datenbank, sondern immer nur mit dem WordPress Backend interagierst: Die Datenbank ist das Herz deiner Website.
Aber wie zuvor erwähnt: Auch User sind in der Lage, Daten in die Datenbank einzutragen. Einen Kommentar schreiben, einen Useraccount anlegen, ein Kontaktformular ausfüllen und absenden – all diese Aktionen generieren Daten, die in die Datenbank abgespeichert werden.
Was aber, wenn jemand diesen indirekten Zugang zu deiner Datenbank nutzt, um schadhaften Code in die Datenbank zu schleusen? Dann spricht man von einer SQL Injection.
Der Gedanke dahinter ist nicht einmal besonders kompliziert: Wenn keine Sicherheitsvorkehrungen bestehen, muss der SQL Code nur in ein Formularfeld eingegeben werden (zum Beispiel beim Schreiben eines Kommentars). Der enthält etwa Zeichen, die für den SQL Interpreter – der dafür zuständig ist, in der Datenbank SQL Befehle auszuführen – eine Sonderfunktion haben. Solche Sonderzeichen, genannt Metazeichen, sind zum Beispiel ; „ ‘ und \.
Das CMS glaubt, es handele sich dabei um harmlose Daten, und übergibt die Eingabe wie gehabt an die Datenbank mit dem Auftrag, sie abzuspeichern. Der SQL Interpreter erkennt den Code anhand der Metazeichen als einen Handlungsauftrag und führt den Datenbankbefehl aus.
Übrigens gilt bei SQL Injections genau wie bei Brute Force Attacken: Es sitzt praktisch nie eine Person allein am Computer und gibt manuell SQL Codes in Formulare ein. Auch diese Attacken laufen über automatisierte Botnetze, die tausende Websites gleichzeitig auf Schwachstellen absuchen und dort zuschlagen, wo sie eine entdecken.
Was kann jetzt passieren?
- Es werden jegliche Authentifizierungsmechanismen umgangen oder die Identität eines bestehenden Nutzers verwendet, um Zugang zu erlangen. Wird beispielsweise ein neuer Adminaccount angelegt, spricht man auch von einem Priviledge Escalation Exploit.
- Auf diese Weise können Daten ausgespäht, verändert oder gelöscht werden. Das ist insbesondere dann kritisch, wenn du einen Onlineshop betreibst und über Zahlungsdaten verfügst.
- Es kann auch die Kontrolle über deine komplette Website und deinen Webspace übernommen werden. Das ist möglich über das Einloggen als Admin. Über das Backend wird die volle Kontrolle über deine Website erlangt – und so kann sie als Spamschleuder missbraucht oder in ein Botnet eingefügt werden, oder einfach Schadcode eingebracht werden.
Subscribe to the Raidboxes newsletter!
We share the latest WordPress insights, business tips, and more with you once a month.
"*" indicates required fields
Fazit: Gerade wegen der Automatisierung sind WordPress SQL Injections sehr gefährlich
WordPress SQL Injections gehören zu den gefährlichsten Hacks überhaupt. Sie sind leicht durchzuführen, meist automatisiert und können massive Schäden anrichten: Gerade für Shops ist die Gefahr durch SQL Injections wegen der Daten in der Datenbank existenziell bedrohlich.
Daher ist es wichtig, deine Website entsprechend zu schützen: Jeglicher Input von außen muss überprüft und gesäubert werden. Zudem solltest du Daten maskieren, um die Ausführung von Schadcode zu verhindern. Dieser Vorgang nennt sich Data Sanitization and Validation und wird beispielsweise im WordPress Developer Guide ausführlich behandelt.
Grundlegend helfen hier auch umfassende Sicherheitsplugins weiter: Denn sie sind insbesondere in der Lage, automatisierte Angriffe auf deine Websites zu blockieren, die die Grundlage für viele Hacks darstellen.
Leave a Reply